|
|
CITS3002 Computer Networks - Tutorial 1
(for the week commencing 11th March 2024)
Please check our Tutorial Timetable →
HERE
Remember, that for this and future tutorials,
you should always demonstrate some technical sophistication and evidence -
answers of the form
"things will be faster", or
"... bigger", or
"... smaller", or
"... cheaper"
are insufficient.
- [from Lecture-1]
In March 2015 Australia's (then) controversial
Telecommunications
(Interception and Access) Amendment (Data Retention) Bill 2015,
was passed into law by the Australian Parliament.
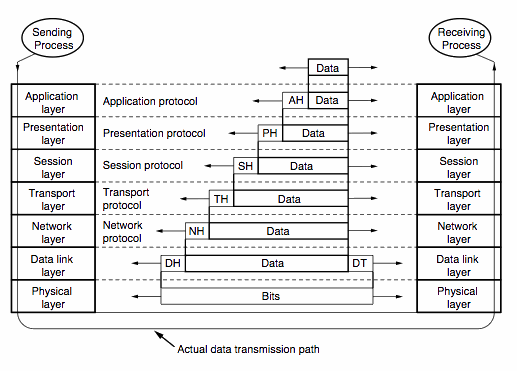
With reference to the ISO/OSI reference model of computer networking,
data from which layers is retained under this Bill?
|
Consider mobile phones as providing an obvious case-study -
the information collected will include:
- who (actually, which device, a phone number or SIM card number)
is calling who (another device);
- what time was the call started, and finished;
- how many bytes of data was transfered;
- BUT NOT the words of the conversation itself.
|
May be of interest:
- [from Lecture-2]
Hamming's method of error correction
can only detect and correct single bit errors.
However,
we saw that it requires 4 additional (redundant) bits to support the 7 data
bits of each ASCII character,
and we consider that overhead to be excessive for normal communications.
Moreover, we know that errors occur in bursts, typically 100 bits long.
Consider the typical need to transmit several kilobytes,
or megabytes,
for a single file-transfer.
How can Hamming's method be adapted to correct burst errors,
without introducing an enormous overhead in additional check bits?
Is your proposed mechanism practical?
- [from a past exam paper]
With the aid of a diagram,
explain how differential Manchester encoding
enables the detection of a collision bewteen
two signals on an Ethernet-based network.
Your diagram does not have to be very accurate,
but it should clearly show how/why the collision is detected.
Chris McDonald
March 2024.
|

