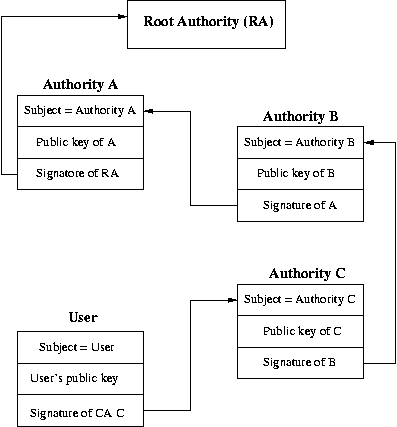
Certificate Path validation
CAs are organized in hierarchies - each parent CA signs a
certificate vouching for a subordinate CA's public key.
When validating a chain of certificates,
the certificate path,
the path is followed until the top of the chain is reached (when?).
There is no automated way of verifying the top of a certificate chain
other than verifying that it is one of a list of directly known (and
implicitly trusted) certificates (such as in a browser).
Several companies,
such as VeriSign, Thwaite, Baltimore, AT&T,
and a growing band of government departments
have positioned themselves 'at the top'.
CITS3002 Computer Networks, Lecture 12, Cryptography's role in networking, p24, 22nd May 2024.
|


 CITS3002
CITS3002 help3002
help3002 CITS3002 schedule
CITS3002 schedule