

|
CITS3002 Computer Networks |
| ← prev |  CITS3002
CITS3002 |
 help3002
help3002 |
 CITS3002 schedule
CITS3002 schedule |
||||
Traffic Shaping - Token Bucket AlgorithmThe leaky bucket algorithm enforces a strict maximum traffic generation. It is often better to permit short bursts, but thereafter to constrain the traffic to some maximum. The token bucket algorithm provides a bucket of permit tokens - before any packet may be transmitted, a token must be consumed. Tokens 'drip' into the bucket at a fixed rate; if the bucket overflows with tokens they are simply discarded (the host does not have enough traffic to transmit).
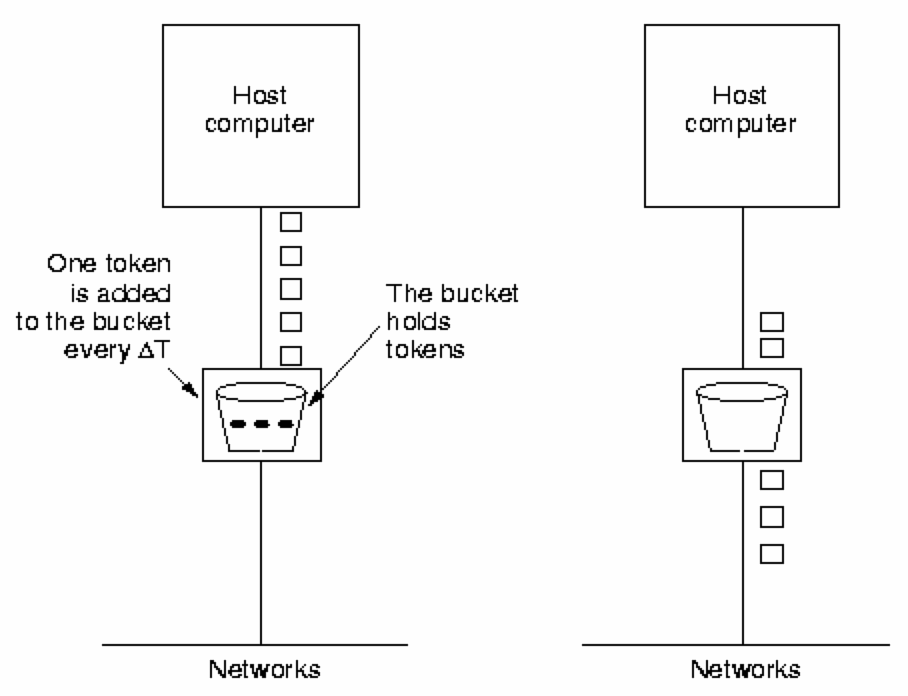 Packets are placed in an 'infinite' queue. Packets may enter the subnet whenever a token is available, else they must wait.
The token bucket algorithm enables an application to generate and
transmit 'bursty' traffic
(high volume, for a short period).
It avoids saturating the network by only permitting a burst of traffic to
continue for a limited time (until the tokens run out).
CITS3002 Computer Networks, Lecture 5, The Network Layer, p21, 25th March 2024.
|