

|
CITS3002 Computer Networks |
| ← prev | next → |  CITS3002
CITS3002 |
 help3002
help3002 |
 CITS3002 schedule
CITS3002 schedule |
|||
Traffic Shaping - Leaky Bucket AlgorithmConsider a leaking bucket with a small hole at the bottom. Water can only leak from the bucket at a fixed rate. Water that cannot fit in the bucket will overflow the bucket and be discarded. Turner's (1996) leaky bucket algorithm enables a fixed amount of data to leave a host (enter a subnet) per unit time. It provides a single server queueing model with a constant service time.
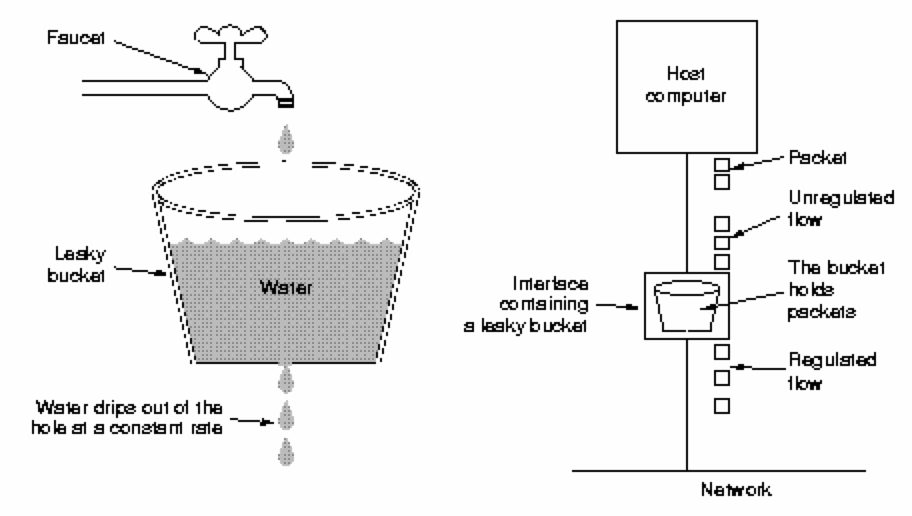 If packets are of fixed sizes (such as 53-byte Asynchronous Transfer Mode cells), one packet may be transmitted per unit time. If packets are of variable size, a fixed number of bytes (perhaps multiple packets) may be admitted.
The leaky bucket algorithm enables an application to generate
traffic which is admitted to the network at a steady rate,
thus not saturating the network.
CITS3002 Computer Networks, Lecture 5, The Network Layer, p20, 25th March 2024.
|