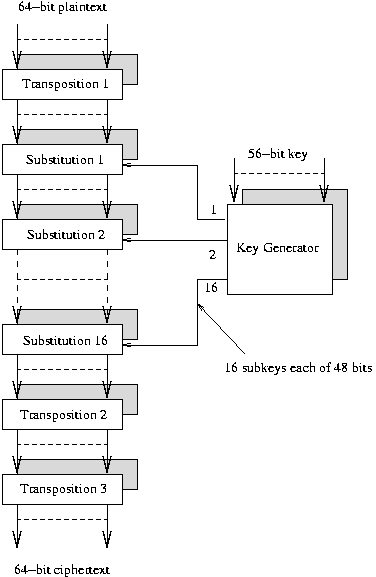
The Steps of the DES Algorithm
The algorithm has 19 steps for encryption; decryption simply performs the
steps in the reverse order.
|
What are the steps of this magic function f?
- E := R1 (which is 32 bits) expanded to 48 bits.
- D := XOR(E, Ki).
- Divide D into 8x6 bits;
feed each of these 6 bits into a different S box each producing 4 bits.
- Feed these 8x4 bits (= 32 bits) through a P box.
How is the DES key used?
- K0 := 56 transposition cipher of K.
- Divide K0 into 2x28 bits.
- ROLeft each part.
- Ki := 56 bit transition of the number formed.
|
CITS3002 Computer Networks, Lecture 12, Cryptography's role in networking, p9, 22nd May 2024.
|


 CITS3002
CITS3002 help3002
help3002 CITS3002 schedule
CITS3002 schedule