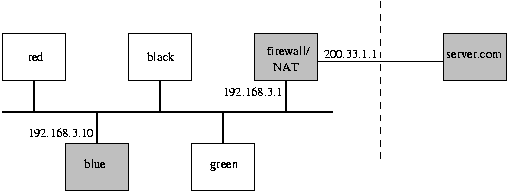
An Example of IP Masquerading
Consider the following example:
Machine blue
(with a single Ethernet interface, and IP address 192.168.3.10)
generates a packet,
from its port 400,
destined for server.com.
When the packet arrives at the NAT-enabled firewall
(on its internal Ethernet interface, IP address 192.168.3.1),
the firewall will de-encapsulate the packet,
and rewrite it so that it appears to have now originated
from the firewall itself
(with IP address 200.33.1.1, and a currently unused port on the firewall, 1430).
The packet is finally forwarded on the external Ethernet
interface.
| SRC computer |
SRC IP |
SRC port |
Firewall's IP |
Firewall's assigned port |
| blue |
192.168.3.10 |
400 |
200.33.1.1 |
1430 |
| black |
192.168.3.22 |
1814 |
200.33.1.1 |
1892 |
| red |
192.168.3.18 |
550 |
200.33.1.1 |
1434 |
| blue |
192.168.3.10 |
4412 |
200.33.1.1 |
1890 |
| green |
192.168.3.19 |
2410 |
200.33.1.1 |
1435 |
When a reply is received from server.com,
its destination IP address will be 200.33.1.1, port 1430.
The firewall's mapping table is consulted to reverse the translation,
changing the IP address to 192.168.3.10 (for blue), port 400.
CITS3002 Computer Networks, Lecture 11, Security of TCP/IP, p26, 15th May 2024.
|


 CITS3002
CITS3002 help3002
help3002 CITS3002 schedule
CITS3002 schedule