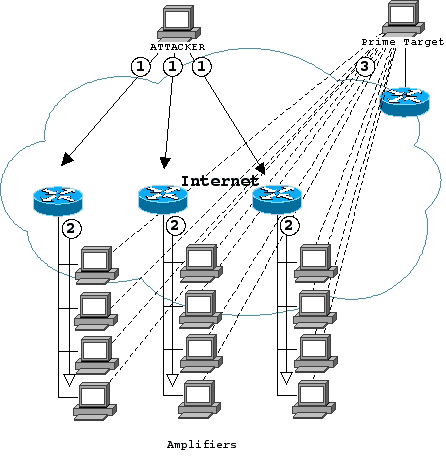
Distributed Denial of Service (DDoS) Attacks
In a distributed denial of service (DDoS) or a packet
storm attack,
an attacker will flood a single system with 'junk' packets to consume
bandwidth - preventing legitimate packets getting through.
Using only a single attacker, the effect of the attack is
greatly multiplied using attack servers termed agents,
zombies, daemons (in the trinoo attacks)
and servers (in the TFN attacks).
Attacks are launched simultaneously from hundreds of 'remote-controlled'
attack servers.
The attacker must first gain access to the hundreds of agent machines,
but will use scripts to locate many machines with the same vulnerability.
A single trojan program will typically be installed on each of the agent
machines, and triggered days or months later by a single UDP or
ICMP packet to the agent.
All agents will then launch their attacks,
using source spoofing, on a single target.
The increased use of ADSL and 'always on' connections,
increases the opportunity of DDoS attacks.
RFC-2267 was written in response to this type of attack,
suggesting that ISPs should filter traffic and drop any packets with spoofed
source addresses. In practical terms, this has proven difficult.
CITS3002 Computer Networks, Lecture 11, Security of TCP/IP, p14, 15th May 2024.
|


 CITS3002
CITS3002 help3002
help3002 CITS3002 schedule
CITS3002 schedule