

|
CITS3002 Computer Networks |
 CITS3002
CITS3002 |
 help3002
help3002 |
 CITS3002 schedule
CITS3002 schedule |
|||||
Automated Development of Distributed ApplicationsThe complications of layering in the OSI model come to a head in the Session Layer and a number of recent developments have 'bypassed' many of the OSI layers. These include, and have been motivated by :
The Remote Procedure Call (RPC) ParadigmThe remote procedure call (RPC) paradigm [BJ Nelson, 1981] and [AD Birrell and BJ Nelson, 1984] is based on the observation that procedure calls are a well understood mechanism for control transfer. The proposal is that procedure calls may be consistently extended to access remote environments (other machines). When a remote procedure call is invoked :
See: Implementing Remote Procedure Calls, Birrell, Andrew D. and Nelson, Bruce Jay, in ACM Trans. Comput. Systems, 2(1), pp39-59, February 1984.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p1, 8th May 2024.
The RPC Execution Order
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p2, 8th May 2024.
The RPC Execution Order, continued
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p3, 8th May 2024.
The RPC Execution Order, continued
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p4, 8th May 2024.
An Example of Transparent AccessConsider an application requiring access to a file available on another machine.
Here, the local operating system kernel recognized that the mount point, /home/uniwa/staff9, refers to a file system on a remote machine and a series of RPC requests are made to access the remote file.
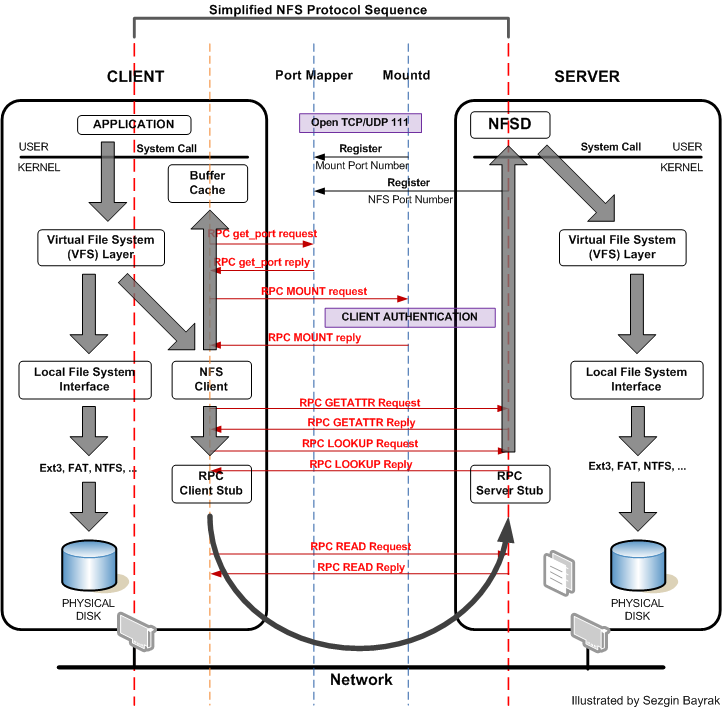
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p5, 8th May 2024.
Passing parameters to remote proceduresSignificant problems are introduced with parameter passing:
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p6, 8th May 2024.
SUN Microsystem's RPC Compiler - rpcgenMany operating systems provide RPC within their kernels and as a standard library of routines. One such example is SUN's implementation of RPC (in [RFC1057]). The RPC package consists of rpcgen, a compiler for creating remote procedure call server and client stubs, the XDR for encoding data into a portable manner between different architectures and a runtime library (provided in C's standard library libc). For example:
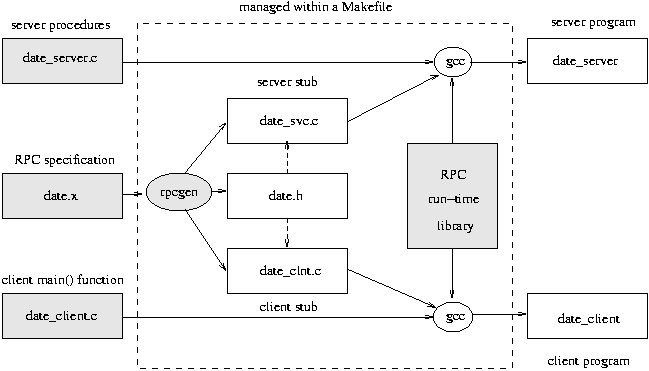
Complete example in rpc_example.zip
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p7, 8th May 2024.
RPC Client-side Code in C
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p8, 8th May 2024.
RPC Server-side Code in C
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p9, 8th May 2024.
Naming and Interface BindingHow does the client-stub know who to call? Most operating systems now supporting RPCs use a replicated database used to store server addresses. When a server restarts (boots) it informs the database that it is alive and passes it :
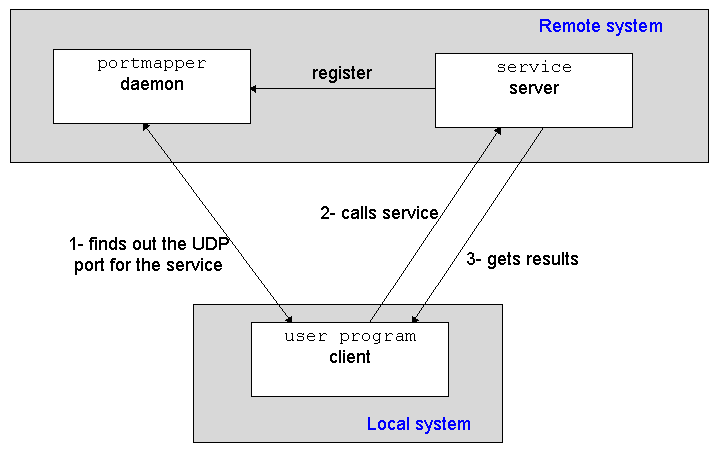
Thereafter, the first time a client-stub needs to locate a remote procedure it first asks the database server (the portmapper). The server maps the procedure's name to the network address. This process is termed binding.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p10, 8th May 2024.
Locating and calling the server

CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p11, 8th May 2024.
Semantics of Remote Procedure CallsIdeally, Remote Procedure Calls look like local procedure calls and the application programs may be unaware of the existence/need for the network. Like everything else, they suffer from network crashes, lost messages and delays. Consider what happens when a server crashes. The client stub may :
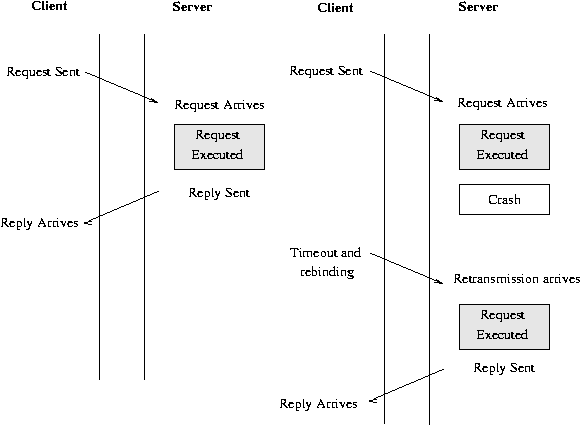
Should clients re-issue their requests in the event of a failure? Moreover, should the client's application (manually) or the client's stubs (automatically) re-issue a request? It is important to understand whether a package supports at-most-once or at-least-once semantics. Remote operations, which may be repeated without consequence, are termed idempotent operations.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p12, 8th May 2024.
The External Data RepresentationThe External Data Representation (XDR) is a standard for the description and encoding of data [RFC1014]. XDR was designed specifically to provide the marshalling and unmarshalling operations for Sun's implementation of RPC. All data which is transferred in RPC is translated using XDR. XDR is also useful in situations which do not use RPC, or even the network, as it allows one to read and write arbitrary C data structures in a consistent and well-defined manner. e.g. We can use XDR to save a program's state (i.e. data structures) to a file so that when the program is restarted it can resume execution where it left off. XDR fits into the ISO presentation layer, and is roughly analogous to ISO's Abstract Syntax Notation.1. The major difference between the two is that ASN.1 explicitly sends typing information along with the data while in XDR this information is implied.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p13, 8th May 2024.
The Differences in Data RepresentationMachines of different architectures represent data differently internally. Simple example: integers On Sun-SPARC or Motorola PowerPC architectures integers are stored as
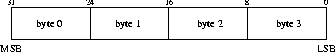
while on Intel x86 processors, integers are stored as

So the integer 1 on a SPARC or PowerPC would be interpreted as the integer 16777216 (224) on the Intel. Other problems occur with respect to alignment and pointers:
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p14, 8th May 2024.
The XDR ApproachXDR takes a canonical approach to data communication: it defines a standard XDR representation for data and makes its clients use it. If a program wishes to use XDR to transmit data it must firstly translate its internal representation of the data to the XDR representation. A program receiving XDR information performs the opposite mapping: it converts the incoming XDR data to its own representation
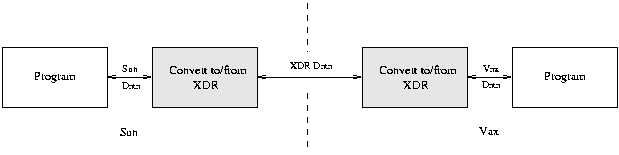
The advent of a new machine/language has no impact on existing users: the new machine is 'taught' to convert between XDR and its own representation and can thereafter communicate with all other XDR users.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p15, 8th May 2024.
The XDR Data Representation
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p16, 8th May 2024.
The XDR Representation, continuedXDR defines the representation of simple types, and the representation to be used when combining these types to produce more complex types. The simple types include:
These may be combined to produce the complex types:
XDR also allows some special types:
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p17, 8th May 2024.
The XDR Representation of some simple typesIntegers:
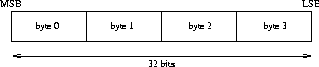
Signed: Two's Complement (MSB is a sign bit).
Reals - Single Precision:
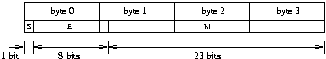
Reals - Double Precision:

S - Sign Bit (0 -> positive)
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p18, 8th May 2024.
The XDR Representation of some complex typesStrings:
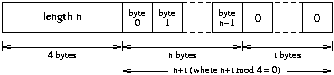
Variable Length Arrays:
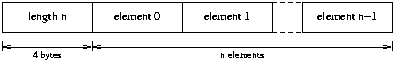
Note that a string is represented more efficiently than an array of characters would be. Fixed Length Arrays:

Structures:
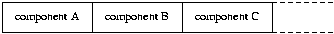
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p19, 8th May 2024.
The SunOS XDR LibraryThe SunOS library contains functions to convert each of the primitive types to/from their XDR representation.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p20, 8th May 2024.
The SunOS XDR Library, continuedExample: The XDR routine to convert an integer is declared as
and then call the function
To decode reading from standard input we would create the stream using
and use the same function call
to receive the integer into variable i.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p21, 8th May 2024.
Converting complex data structuresExample: If we wished to XDR encode a structure of the form
we could use the following XDR conversion function
If we had an array of person structures, declared as
we could convert it using
The final parameter is the name of the function which is to be called to XDR encode each element of the array.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p22, 8th May 2024.
Converting complex data structures, continuedExample: If we wished to XDR encode a pointer to the person structure declared as
we would convert it using
If the XDR stream indicates an encode operation the function follows the pointer and encodes the data it points to by calling xdr_person(). If the XDR stream indicates a decode operation and *pp is NULL the routine allocates memory to hold the structure and makes pp point to that area. The routine then decodes the data by calling xdr_person() and places the decoded structure into the memory pointed to by pp. A related routine called xdr_pointer() exists which more correctly understands NULL pointers. This facility can be used to create functions which encode/decode linked lists and other arbitrarily complex data structures.
CITS3002 Computer Networks, Lecture 10, Architecture independent applications, p23, 8th May 2024.
|