

|
CITS3002 Computer Networks |
 CITS3002
CITS3002 |
 help3002
help3002 |
 CITS3002 schedule
CITS3002 schedule |
|||||
Internet Transport Layer ProtocolsTo date, we've compared the 7-layered OSI/ISO model to the 4-layered TCP/IP protocol suite. We've recently focused on how TCP/IP delivers its packets - using 32-bit IPv4 addresses to deliver data, first to the correct network, and then to the correct host on that network. We've also focused on how the protocols are embedded, or encapsulated, within each other: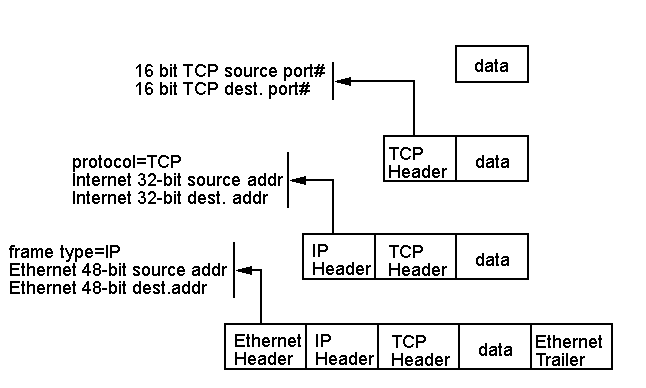
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p1, 24th April 2024.
Port numbersIP addresses, alone, are not enough as they only address hosts, and not individual operating system processes on those hosts. From the perspective of any transport protocol, such as TCP (next), each arriving frame is further identified by a 16-bit positive port number that identifies the 'software end-point' to receive the payload. One role of TCP is to demultiplexed each arriving segment to its corresponding communication end-point, using a port as an index. Port numbers below 1024 are described as reserved ports, and on operating systems with distinct users and privilege levels, elevated privilege ('root' or 'administrator' access) is required to create a 'software end-point' bound to such ports. The file /etc/services on Linux and macOS, or C:\Windows\System32\drivers\etc on Windows, lists ports commonly used (worldwide), and ports in use for dedicated/local applications:
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p2, 24th April 2024.
The Transmission Control Protocol (TCP)The Transmission Control Protocol (TCP) transforms the 'raw' IP into a full-duplex reliable character stream [Ref:RFC 793]. TCP uses a 'well-understood' sliding window with selective-repeat protocol, and conveys a number of important fields in its TCP frame header:
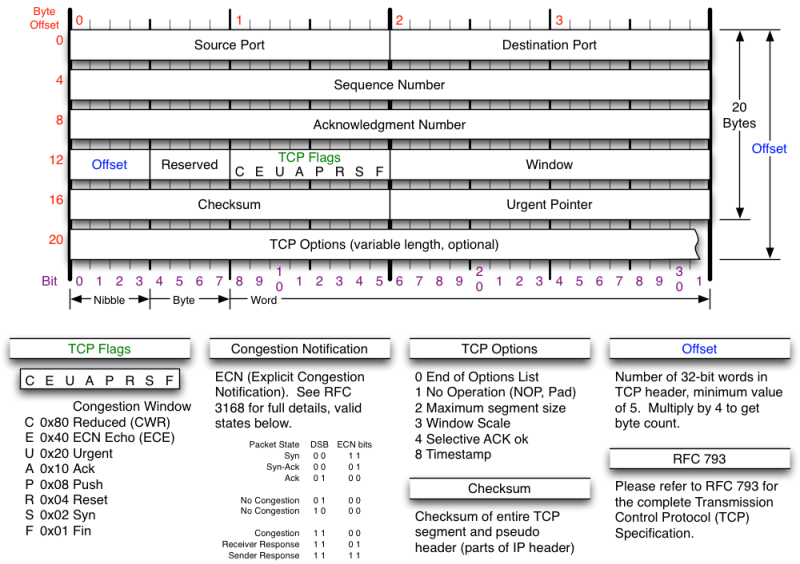
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p3, 24th April 2024.
What TCP/IP Provides to ApplicationsTCP/IP provides 6 major features:
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p4, 24th April 2024.
TCP/IP 3-way connection establishment and sequence numbers
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p5, 24th April 2024.
TCP/IP RetransmissionsTCP/IP is employed between processes physically tens of centimetres (i.e. nano-seconds) apart, as well as processes tens of thousands of kilometres (near a second) apart. As TCP/IP uses a sliding window protocol, timeouts are employed to force re-transmissions. As there are so many destination hosts, what should be the timeout value? To cope with the widely varying network delays, TCP maintains a dynamic estimate of the current round trip time (RTT) for each connection. Because the RTTs vary tremendously, TCP averages RTTs into a smoothed round trip time (SRTT) that minimizes the effects of unusually short or long RTTs.
where α is a smoothing factor that determines how much weight the new values are given. When α=1, the new value of RTT is ignored, when α=0 all previous values are ignored. Typically α is between 0.8 and 0.9. The SRTT estimates the average round trip time. To also allow for queuing and transmission delays, TCP also calculates the mean deviation (MDEV) of the RTT from the measured value. This is also smoothed:
RTO = SRTT + 2 x SMDEV
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p6, 24th April 2024.
TCP/IP Congestion ControlPerhaps the most important, and certainly the most studied and 'tinkered with' aspect of TCP/IP is its congestion control. TCP attempts to avoid congestion collapse by using end-to-end packet loss as the metric of congestion.
In combination with its closely related slow-start algorithm for new connections, TCP is capable of both avoiding and recovering from most congestion. Ref: RFC 2001.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p7, 24th April 2024.
Network Application Program Interfaces (APIs)Dating back to early operating system implementations, applications attempted to provide a common framework to access both files and devices. Calls to Unix open() return a file descriptor which is then used in calls to read() and write(). It is preferable if the application program interfaces (API) to network I/O exhibit the same semantics as file, or stream, I/O, but this is difficult for a number of reasons:
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p8, 24th April 2024.
An Example Network API - Berkeley SocketsSockets are a generalization of the original Unix file system model. The most important difference is that the operating system binds file descriptors, once, to files and devices when they are opened. With sockets, applications can specify the destination each time they use the socket. When sockets were first proposed (1982 in 4.1cBSD), it was unclear how significant TCP/IP would become. As a (beneficial) consequence, sockets have been designed to use many different protocols.
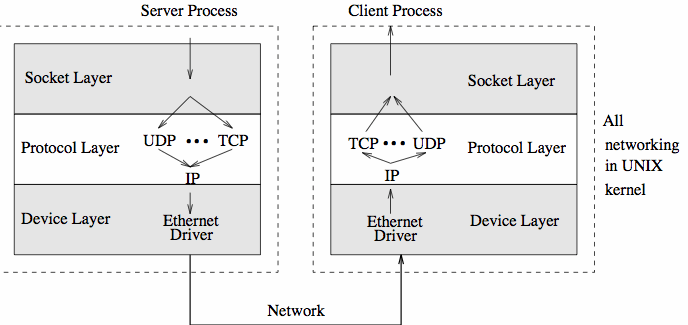
The current (kernel) socket implementation consists of three parts :
Essential reading: A Guide to Network Programming using Internet sockets, by Brian "Beej" Hall.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p9, 24th April 2024.
Domain AddressingLegal combinations of protocols and drivers are specified when the kernel is configured. For example, sockets that share common communication properties, such as naming conventions and protocol address formats, are grouped into address families. The Linux file /usr/include/bits/socket.h lists all supported address families.
Processes communicate using the client-server paradigm. A server process listens to a socket, one end of a bidirectional communication path and the client processes communicate with the server over another socket, the other end of the communication path. The kernel maintains internal connections and routes data from client to server.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p10, 24th April 2024.
Establishing Sockets With OS System CallsThe socket mechanism requires several Unix system calls. The socket() call establishes an end point of a communications link.
protocol is usually 0 to indicate the default for the family/type combination. The socket() system call returns a small integer, termed a socket descriptor, (akin to a file descriptor). The call may fail due to a request for an unknown protocol or when a request is made for a type without a supporting protocol.
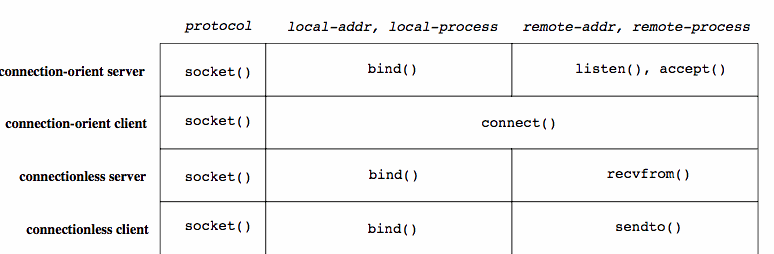 The socket() system call only instantiates protocol from the 5-tuple association. Depending on whether the socket is being used in the client or server of either a connection-oriented or connectionless communication, different programs do different things next:
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p11, 24th April 2024.
Naming SocketsWhen initially created a socket is unbound (it has no addresses associated with it). Communication cannot occur on an unbound socket - without a name for the process owning the socket, the kernel cannot demultiplex packets to the correct socket. The bind() routine provides an address (a name) to the local end of the socket.
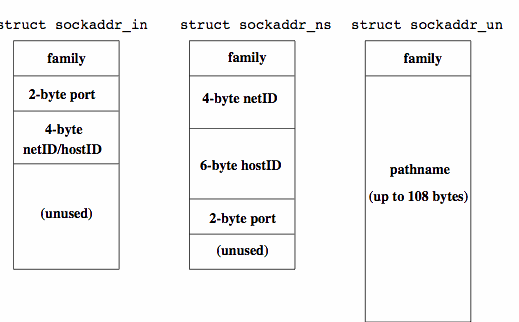
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p12, 24th April 2024.
Naming Sockets, continuedThe related call connect() takes the same arguments but binds an address to the remote end of the socket. For connectionless protocols, such as UDP/IP, the kernel caches the destination address associated with the socket. Server processes bind address to sockets and 'advertise' their names to identify themselves to clients. Connection EstablishmentServers accept connections from remote clients and cannot use connect() because they do not (usually) know the address of the remote client until the client has initiated a connection. Applications use listen() and accept() to perform passive opens. When a server arranges to accept data over a virtual circuit, the kernel must arrange to queue requests until they can be serviced.
When accept() returns, from contains the network address of the remote end of the socket, and new_socket is in a connected state.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p13, 24th April 2024.
System Call Sequences for Connection-oriented and Connectionless I/O
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p14, 24th April 2024.
A Client Process in the Unix Domain (in C)Consider a simple client process wishing to establish a connection with a server process in the Unix domain. When communicating within the Unix domain, the data frames never leave the single computer, and never get lost (other than on an extremely busy machine). In this example, the client program sends commands to a 3D printer which is directly connected to the same computer. The client process simply connects to the server process and then writes the bytes to be printed to the socket (note that this example is far from how print spooling works in practice!)
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p15, 24th April 2024.
A Server Process in the Unix Domain (in C)Now consider our server process which accepts streams of bytes (commands and contents) to be printed on our 3D-printer. To avoid contention for the printer, and to possibly screen the requests, a single server performs the printing.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p16, 24th April 2024.
A Remote Login Client (Internet Domain, in C)Most operating systems, supporting internetworking using the Berkeley sockets API, also provide many functions to facilitate access to many commonly required resources - such as hostnames, protocol numbers, service numbers, etc. In an environment where many computers require access to consistent data, these API functions, themselves, may be configured to seek their information via the Internet.
CITS3002 Computer Networks, Lecture 8, Transport layer protocols and APIs, p17, 24th April 2024.
|