

|
CITS3002 Computer Networks |
 CITS3002
CITS3002 |
 help3002
help3002 |
 CITS3002 schedule
CITS3002 schedule |
|||||
The Requirements of InternetworkingNetworks come in differing topologies and speeds and (of course) no single network configuration suits everyone.
The technology known as internetworking draws the multitudes of networking technologies into a common framework that combines networks into internets. In general an internetwork must :
Easy really!
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p1, 17th April 2024.
A Brief History of the InternetIn 1969, the US Defense Advanced Research Projects Agency (DARPA) funded a project in computing resource sharing termed the ARPANET. ARPANET consisted of multiply connected, high-bandwidth (56 Kbps) links between government, academic and industrial laboratories. During the 1970s DARPA was the chief funding body for packet switching networks using diverse technologies, such as mobile radio transmitters and satellite links. By the mid 1970s research concentrated on a framework for the ARPANET. By 1979 the Transmission Control Protocol/Internet Protocol (TCP/IP) was running exclusively over ARPANET.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p2, 17th April 2024.
The Initial Internetting Concepts
The Internet Society hosts a monograph named
A Brief History of
the Internet, by Vint Cerf etal..
Quoting directly from that paper (READ IT!):
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p3, 17th April 2024.
The Initial Internetting Concepts, continuedEmergent basic approaches:
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p4, 17th April 2024.
(Earlier) Milestones in Internet HistoryCerf's paper notes these key milestones in Internet history:
DiscussionWhat advances were made over the next 30+ years? Would you classify them as technical or societal?
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p5, 17th April 2024.
Where It All Began (?)
Internet RFCs (Requests For Comments)The Internet is not (yet) a commerical product - instead a large, active research project. Reports of work, proposals for protocols, and protocol standards appear as a series of nearly 8800 technical reports termed RFCs. Recently: RFC 9233: Internationalized Domain Names for Applications 2008 (IDNA2008) and Unicode 12.0.0. The whole RFC collection may be searched and read via: (and read the collection of humorous April Fools' Day Request for Comments).
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p6, 17th April 2024.
The TCP/IP Protocol Architecture
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p7, 17th April 2024.
The TCP/IP Protocol Architecture, continued
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p8, 17th April 2024.
Traditional Class-based IP Version 4 AddressingEach computer or device accessible using Internet (IP) protocols has at least one unique address within its subnet. If every device was accessible over the global Internet, each device would require its own unique address (worldwide); each address consists of a network 'portion' and a local 'portion'. The network 'portions' are assigned by the central DARPA authority. The original Internet designers were unsure as to how the Internet would grow - either a large number of networks each with a small number of hosts or a small number of networks each with a large number of hosts. As a compromise, Internet addressing schemes accommodate both large and small network topologies.
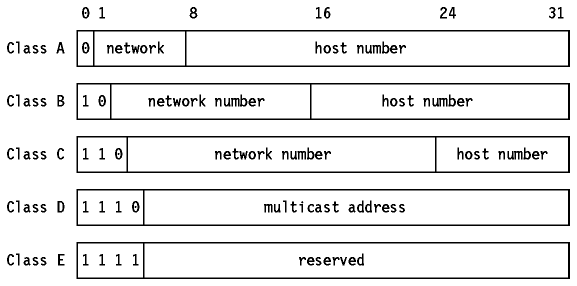 Moreover, class-based addresses are self-describing.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p9, 17th April 2024.
Class-based IP Version 4 Addressing, continuedWhen describing Internet addresses (verbally or in literature) a dotted decimal notation is used to describe the 32-bit addresses.
#
130.95.1.10 www www.csse.uwa.edu.au
130.95.1.8 budgie budgie.csse.uwa.edu.au
130.95.116.32 laser25 laser25.csse.uwa.edu.au
#
130.95.252.64 ecm-csse2101-l.uniwa.uwa.edu.au
130.95.252.112 ecm-csse2101-x.uniwa.uwa.edu.au
The different (hardware) encoding of 32-bit integers between architectures
demands a standard representation for Internet addresses.
The Internet standard for byte order specifies that integers are sent most
significant byte first (big-endian).
Jonathan Swift's
Gulliver's Travels, published in 1726,
provided the earliest literary reference to computers,
in which a machine would write books.
This early attempt at artificial intelligence was characteristically
marked by its inventor's call for public funding and the employment of
student operators.
Gulliver's diagram of the machine actually contained errors,
these being either an attempt to protect his invention or the first
computer hardware glitch.
The term endian is used because of an analogy with the story Gulliver's Travels, in which Swift imagined a never-ending fight between the kingdoms of the Big-Endians and the Little-Endians (whether you were Lilliputian or Brobdignagian), whose only difference is in where they crack open a hard-boiled egg.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p10, 17th April 2024.
Classless Inter-Domain Routing (CIDR)With the advent of CIDR, the classful restrictions no longer exist. Address space may be allocated and assigned on bit boundaries, and routers may use one aggregated route (like 194.145.96.0/20) instead of advertising 16 class C addresses [RFC-1518].
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p11, 17th April 2024.
Mapping Internet Addresses to Physical AddressesAn obvious question is 'What physical address should the sender use to send Internet datagrams to a specific Internet site?' In some cases a physical address may fit into, say, a Class A Internet address, but more typically an Ethernet address (48 bits) will not fit in the Internet addressing schema.
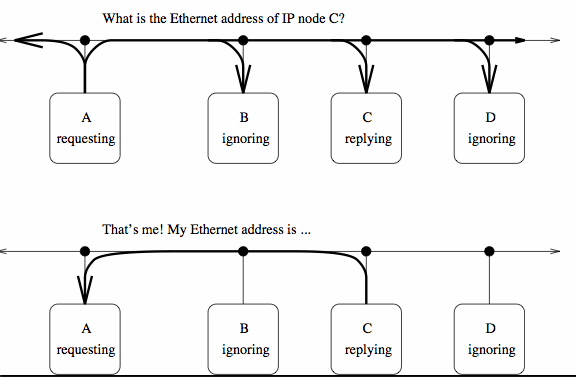 The Address Resolution Protocol (ARP) is a special protocol designed to map Internet to physical addresses. When a gateway needs to know the physical address for an Internet address of a host known to be on its network, it broadcasts an ARP frame requesting the physical address. The required host replies; the gateway caches the address for future reference.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p12, 17th April 2024.
The Address Resolution Protocol (ARP)ARP is a low-level protocol that hides the underlying physical addressing, permitting one or more Internet addresses to be assigned to each machine. ARP is considered part of the physical network system, not strictly part of the Internet protocols.
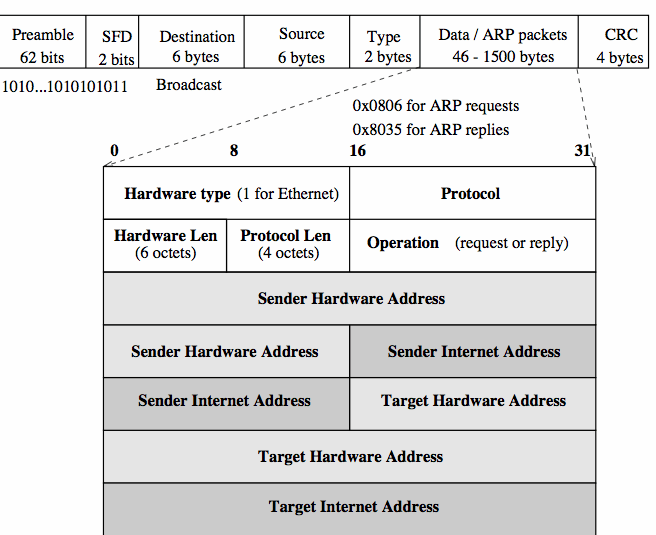 Unlike most protocols, ARP does not have a fixed format. Its design permits it to indicate how big its own fields will be, in this case that Ethernet addresses are 6 bytes (octets) long, and Internet addresses 4 bytes long. This permits ARP to be used with arbitrary network addressing schemes. When making a request, the sender (making the request) also supplies its own Ethernet/Internet address mapping. As all hosts on the Ethernet monitor the broadcast, they can update their mapping tables for future reference (ARP snooping).
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p13, 17th April 2024.
Configuration of Network DevicesAll previous discussion on internetworking has assumed that our computers have been 'up and running', and possessed full knowledge about their networking environment. Where did this knowledge come from? The standard booting sequence for most operating systems involves the computer's hard-disk (or CD-ROM, flash-memory, ...) providing a short bootstrap program of several hundred bytes, which in turn reads the true operating system code from nominated blocks on permanent media. To configure its network connection, a client host requires (at least):
A reasonable first approach to defining this information is in a configuration file (see our labs' /etc/sysconfig/network*):
DEVICE=eth0
BROADCAST=130.95.1.255
NETMASK=255.255.255.0
IPADDR=130.95.1.8
BOOTPROTO=none
GATEWAY=130.95.1.41
GATEWAYDEV=eth0
HOSTNAME=budgie.csse.uwa.edu.au
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p14, 17th April 2024.
Problems With Static ConfigurationThere are a number of clear problems with static configuration of network attributes:
A partial solutionThe most 'stable' attribute in most networking configurations is the network interface card's MAC address, such as a card's 48-bit Ethernet address. (many new Ethernet cards can change their MAC addresses programmatically - a mixed blessing!) As with the ARP protocol described earlier, a newly booted client computer can broadcast its Ethernet address via the Reverse Address-Resolution Protocol (RARP). The client broadcasts its RARP request, and any host acting as a RARP server may reply with the client's allocated IP address.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p15, 17th April 2024.
The Bootstrap Protocol (BOOTP)
Booting over a NetworkAn additional feature of BOOTP is its support of providing a computer's (or any 'dumber' device's) operating system's image:
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p16, 17th April 2024.
Dynamic Host Configuration Protocol (DHCP)DHCP's purpose is to enable individual computers on an IP network to extract their configurations from a server (the 'DHCP server'). In general, the servers will have no static information about the individual client computers until information is requested. Responses to each client will then be generated dynamically. The overall purpose of this is to reduce the work necessary to administer a large (often dynamic) IP-based network. The most significant piece of information distributed in this manner is the IP address. DHCP is based on BOOTP and maintains some backward compatibility. The main difference is that BOOTP was designed for manual pre-configuration of the host information in a server database, while DHCP allows for dynamic allocation of network addresses and configurations to newly attached hosts. Additionally, DHCP allows for recovery and reallocation of network addresses through a leasing mechanism.
DHCP, like BOOTP, runs over the user-datagram protocol (UDP),
using ports 67 and 68,
and is defined in
RFC-1534
and
RFC-2131.
DHCP ConfigurationThe DHCP daemon (process) is typically provided with the name of a network interface (such as eth0) so that it knows from where to accept broadcast requests. The DHCP daemon reads information from a configuration file storing the 'public' information for clients. To provide a truly dynamic configuration, we also need to provide a range of IP addresses given to clients. We can also use DHCP to provide fixed configuration information, based on the Ethernet (MAC) address of the arriving request:
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p17, 17th April 2024.
The TCP/IP Protocol DependenciesThe many Internet protocols naturally depend on each other, that is they demand the services provided by other protocols.For example, the file-transfer protocol (FTP) demands that it operates over a reliable stream protocol (TCP), delivered to a host on a network (IP) which provides flow control (ICMP).
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p18, 17th April 2024.
Internet Protocol (IP) DatagramsThe Internet Protocol (IP) provides an unreliable, best-effort, connectionless, packet delivery system. In this unit we will initially be discussing Internet Protocol version 4 (IP v4) RFC-791. Internet datagrams resemble 'standard' physical-layer frames, but are designed to be encapsulated within the normal network framing schema. Hence, Internet datagrams are said to run on top of traditional networks.
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p19, 17th April 2024.
Internet Control Message Protocol (ICMP)ICMP allows gateways and hosts to exchange bootstrap and error information. Gateways send ICMP datagrams when they cannot deliver a datagram, or to direct hosts to use another gateway. Hosts send ICMP datagrams to test the 'liveness' of their network. As an example, the Unix program ping sends ICMP echo messages to a specified machine. Upon receipt of the echo request, the destination returns an ICMP echo reply. ping hence both checks that a host is up and that the path to a host is viable.
prompt> /bin/ping elvis
elvis is alive
prompt> time /bin/ping sophia.inria.fr
sophia.inria.fr is alive
3.006s real 0.040s usr 0.060s sys
prompt> time /bin/ping sophia.inria.fr
sophia.inria.fr is alive
0.591s real 0.020s usr 0.090s sys
If a gateway must discard a datagram due to lack of resources it sends a source quench to the datagram's sender. If a datagram cannot be delivered because a host is down or no route exists, a ICMP destination unreachable datagram is generated. The TCP/IP Protocol suite defines over 25 (in-use) ICMP error message types, including:
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p20, 17th April 2024.
Interesting Uses For ICMP - TracerouteTraceroute utilizes the IP protocol `time to live' field and attempts to elicit an ICMP TIME_EXCEEDED response from each gateway along the path to some host:
CITS3002 Computer Networks, Lecture 7, The TCP/IP protocol suite, p21, 17th April 2024.
|